Services
Our Services
Currency Conversion
Supporting over 60 currencies globally including major currencies such as GBP, EUR & USD and exotic currencies from emerging markets.
API
NOAH Checkout simplify your checkout process
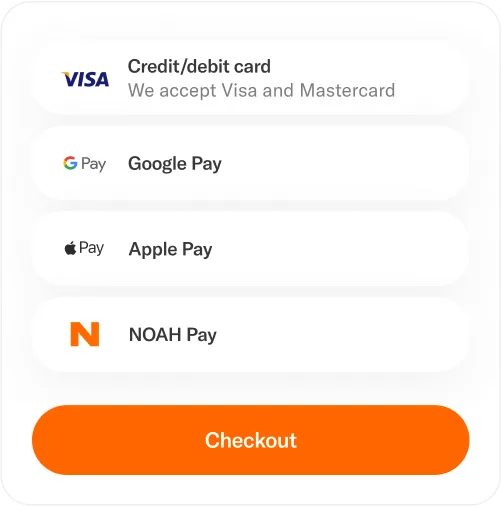

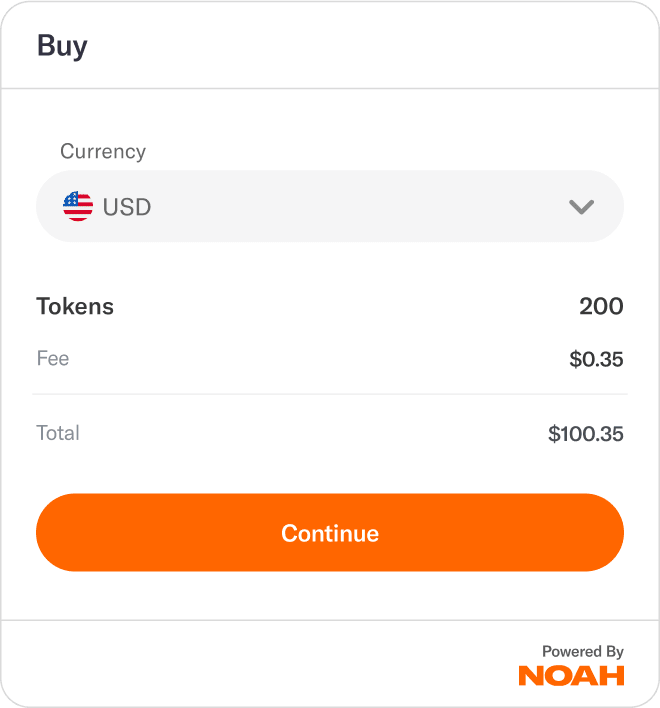
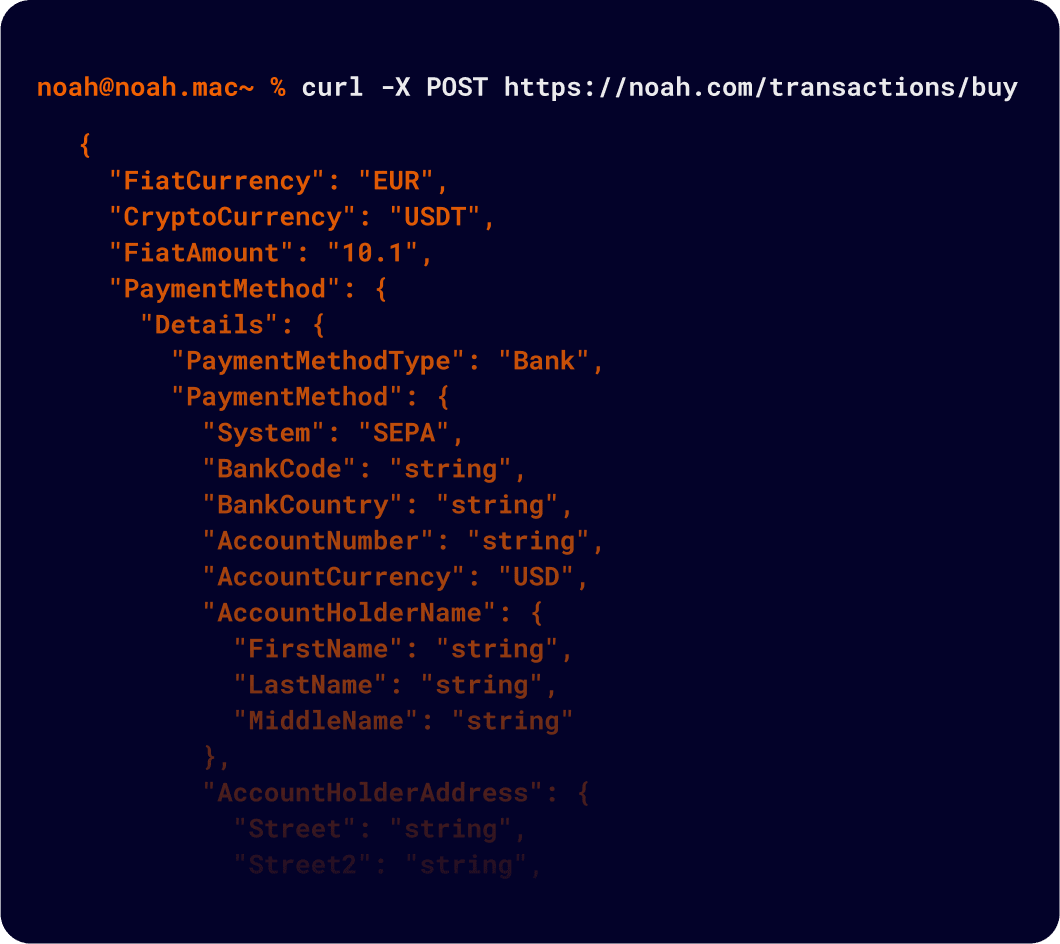
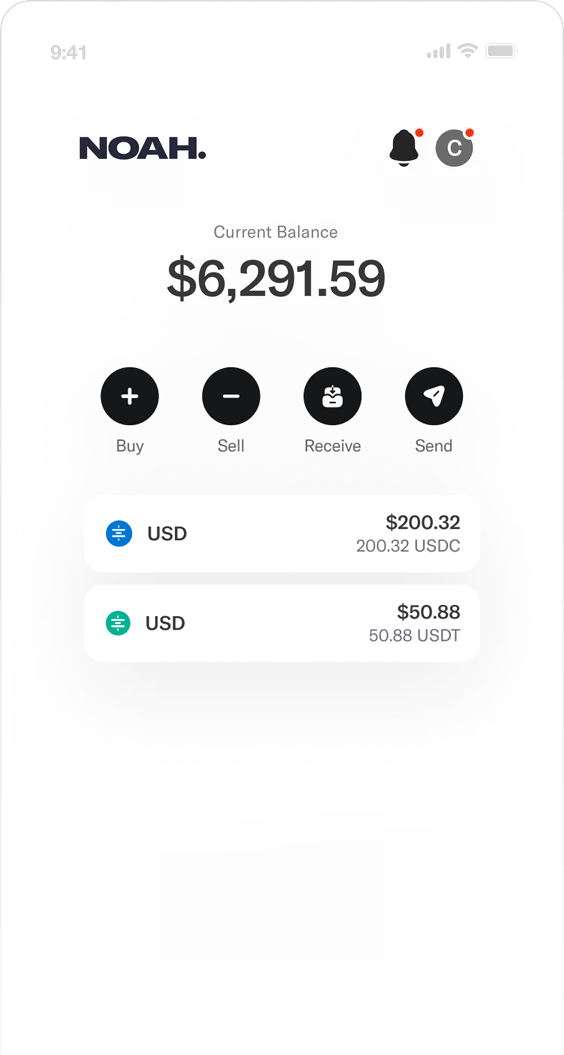
Services
NOAH's advantages over traditional banking services
NOAH's Payment Solution redefines your banking options, by using the power of blockchain combined with traditional banking to provide global reach from one platform.

Compliance and security
Our modern anti-money laundering (AML) and transaction monitoring systems work together to prevent illicit activities, while a strong custody framework ensures the security of your assets.

On and off ramp capabilities
By seamlessly integrating modern rails with top-tier traditional financial services we enable you to expedite cross-border transactions, streamline B2B payments, and hassle-free treasury operations, across +60 currencies globally.

Pricing and speed
We leverage digital assets, to accelerate payments speed, lower fees, and avoid delays inherent in traditional systems. Enabling rapid liquidity flow in and out of global markets and ensuring reliable settlement within 24 hours.
