For a long time payroll stayed tucked into the background. The work was important, but the attention around it never kept pace. People trusted the tools they already had. Checks went out, spreadsheets stayed sealed, nothing obviously alarming happened. Leaders believed that meant the system underneath was still holding together.
That confidence does not survive the way payroll moves now. The environment changed faster than most teams realized. Cloud platforms started talking to one another. Integrations multiplied. Contractors scattered across time zones. Vendors added features that pulled more data than the one they replaced. The whole thing picked up new paths that no one originally planned for.
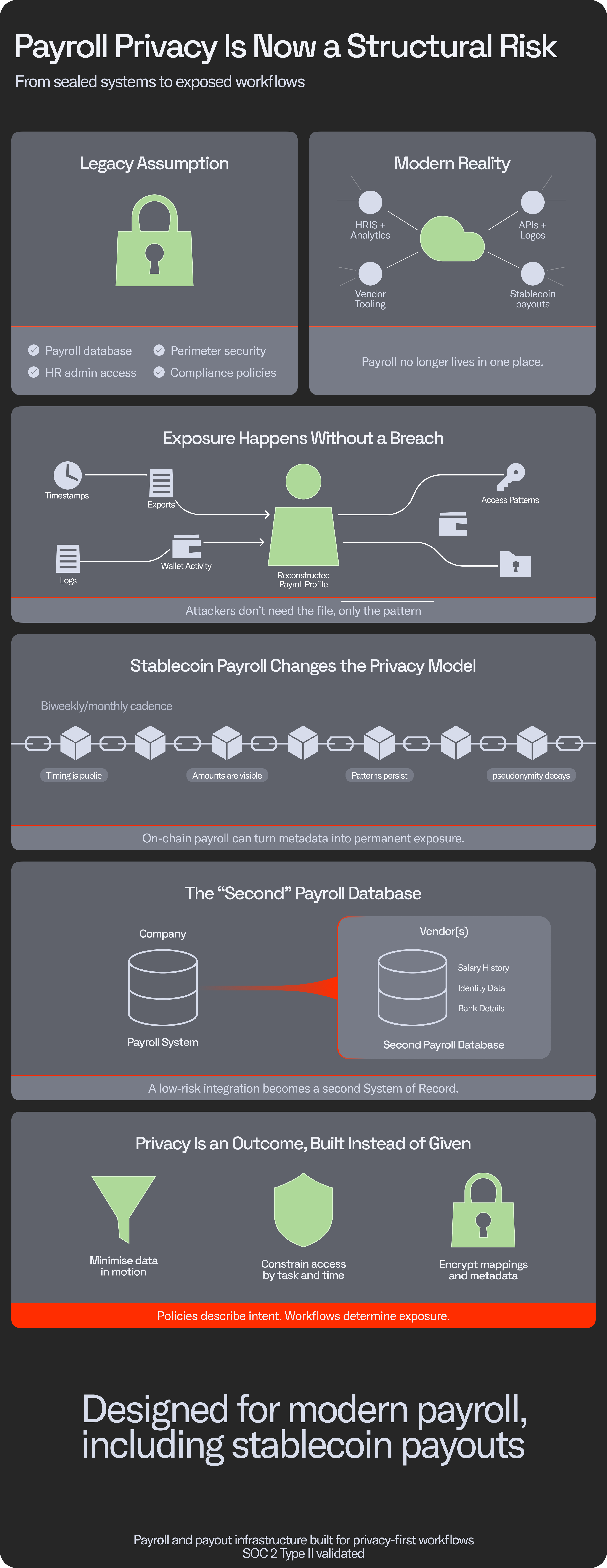
Today, payroll travels in ways that old controls were never designed to follow. It crosses borders, touches systems that were built for convenience over discipline. It ends up exposed inside vendor tooling because someone needed a quick fix during onboarding. It bubbles up in analytics layers that have no business viewing legal names or routing numbers.
Payroll data vulnerability isn’t limited to SaaS connections either. Digital money rails (including third-party fintechs and stablecoins) are increasingly used for contractor payments and global team disbursements. When companies discover fields sitting inside unexpected places, everyone in the room goes silent for a moment.
Some still envision a clean security “perimeter” around payroll.
That picture belongs to a world that evaporated over years. There is no sealed boundary anymore. Reality now unfurls where people rely on fast-moving SaaS stacks, and a large portion of daily operations happens outside the “payroll database”.
Modern exposure spans breaches, fragments that drift through the edges of interconnected systems, and human “error codes” that result in compromised credentials. A timestamp that reveals payroll activity. An export that includes more than anyone remembers authorizing. A vendor log that stores readable values. A dashboard that started simple and turned into a backdoor for inference.
You do not need the full dataset to harm enterprises. You only need the breadcrumbs that let an attacker rebuild the shape.
The part that surprises new leaders most is how little this resembles negligence. It looks like normal work. Rushed work, perhaps, improvised work. Years of “we will clean this up later” work.
This is why payroll privacy stops being a compliance task and starts becoming a structural risk issue. It changes how a company thinks about access, trust, culture, and regulatory exposure. It changes the conversations security teams have with HR and finance. It changes who carries the burden when something leaks.
The Rise of Inference Risk
Payroll is one of the most sensitive datasets a company keeps. It includes personally identifiable information such as: legal identities, banking information, compensation histories, tax identifiers, and years of employment metadata. On their own, these fields are manageable. Combined, they create a potentially threatening personal identity profile.
Modern attackers rarely need a full payroll dump. They use metadata instead. They follow timestamps, vendor logs, analytics exports, misconfigured dashboards, or API signatures. A single poorly scoped integration can reveal more about payroll activity than the payroll team sees in an entire quarter.
Metadata can additionally be combined with stablecoin movements to de-anonymize pseudononymous information, including wallet addresses, and identify individual payroll disbursements or asset holdings.
Shopify Payroll Visibility Incident
In 2020, Shopify disclosed that two support employees misused internal access to view transactional merchant data. Payroll information was not part of the exposure, but the incident revealed something more important. The employees accessed far more internal data than anyone realized they could.
At one point, certain support roles had access to customer order values, merchant identifiers, internal notes, and associated email addresses. This was not a breach in the classic sense. It was an internal visibility failure where broad access behaved like a privacy leak.
Had salary, identity, or banking details been tied to the same roles, the outcome would have been far worse. It demonstrated how quietly permissions can drift and how damning overbroad access becomes in modern systems.
This is the modern payroll landscape. The visibility gaps that make internal systems fragile are amplified where systems connect with public networks that synchronize timing and financial signals which cannot be erased or hidden.
When Payroll Moves Onchain, the Privacy Model Breaks
Companies that use public blockchains for payroll or contractor payouts must contend with an entirely different visibility model. Blockchains do not hide timing, amounts, or patterns. Payroll has a cadence that is easy to recognize. Biweekly cycles, monthly vesting events, quarterly bonuses.
These rhythms identify themselves immediately. Even wallet rotation does not guarantee anonymity. One mistake, such as reusing an address, depositing to a KYC exchange, can torch years of pseudonymity.
Once a single identity is tied to an address, the entire payroll history becomes interpretable. Raises, bonuses, cliff dates, off-cycle adjustments, and even internal mobility become transparent.
Onchain payroll is not inherently unsafe, but it requires deliberate privacy engineering. Without privacy, employers supply sensitive data that can link employees to their onchain compensation profile.
Legacy Payroll Systems Struggle With Modern Threat Models
Most payroll software in use today was designed long before modern cloud architecture, API-driven ecosystems, distributed work, or blockchain rails existed. These systems assume that the office network is the boundary, that administrators need broad and durable visibility, that workflows remain contained, and that vendors have properly limited access.
All of those assumptions fail under modern conditions. Legacy payroll stacks typically suffer from:
- overly broad admin roles
- perimeter-based trust
- years of retained sensitive data
- vendor sprawl with unclear exposure
- fragmented or incomplete auditability
- no concept of wallet rotation or onchain inference
These limitations do not reflect poor engineering. They reflect design assumptions from a wholly different era. Perimeter-based trust is not compatible with SOC 2.
Maintaining SOC 2 Type 2 compliance requires regular reviews of access controls, “least-privilege”, and “just-in-time” access to production systems. Noah authenticates every request, and internal trust is based on identity and policy, not location, as part of our “Defense in Depth” strategy. We only retain data as long as required by regulators.
Implementation (Not Policy) Defines Modern Payroll Privacy
Policies describe what companies want. Policies do not govern what actually happens, until the implementation is built to the spec provided by policies. The organizations that meaningfully limit payroll exposure do so by reshaping workflows, not simply tightening policies. They build around several core principles:
Minimize what the workflow needs
Sensitive fields appear only when a task explicitly requires them. This single design choice eliminates large categories of risk.
Align access with specific tasks
Permissions expand for the duration of a workflow and contract again. Job titles do not drive visibility. Task boundaries do.
Apply encryption throughout the workflow
Sensitive fields stay encrypted as they move. Logs do not contain readable values. Exports are masked or sealed. Decryption occurs only inside narrow execution paths.
Integrate privacy into the design, not as an afterthought
A low-exposure system is created upstream by limiting how much sensitive data ever enters the workflow.
Treat onchain mapping as a high-sensitivity asset
Wallet to identity mappings must be encrypted, compartmentalized, and access-controlled.
A Sterilized Case Study: The Vendor Nobody Realized Was Storing Payroll Data
A large international employer discovered in 2023 that one of its long-standing HR vendors had been quietly retaining a far broader slice of payroll-adjacent data than anyone inside the company understood. The vendor originally handled only employment verification and eligibility checks. Over several contract renewals, its ingestion scope expanded until it quietly accumulated a near-complete identity and compensation profile for a significant portion of the workforce.
Most of this drift was invisible internally. The vendor received structured data feeds for eligibility checks, but over time those feeds began to include salary history, prior bank information, dependent records, and tax identifiers because the upstream systems generating the exports pulled everything by default. No one revisited the integration after the original implementation, and the vendor’s system never pushed back on receiving unnecessary fields.
When the vendor later experienced a security incident involving its own file transfer environment, the employer discovered that the vendor was storing high-sensitivity payroll data far beyond the company’s formal retention window.
What the employer believed was a narrow, low-risk connection had evolved into a secondary repository of payroll identity data that existed entirely outside the organization’s visibility. The exposure did not originate from the employer’s systems. It originated from integration drift, over-broad exports, and a vendor quietly becoming a shadow copy of the payroll database.
Nothing in this scenario was malicious. It was the natural consequence of years of unnoticed scope expansion and a workflow that never revalidated which fields should have been shared in the first place.
Payroll and payout workflows are treated as financial infrastructure, not administrative plumbing, with privacy enforced through minimization, constrained access, and disciplined handling of metadata even when stablecoin payouts are involved. Noah’s SOC 2 attestation is independent validation that these controls operate continuously across real systems and real workflows.